Using KeePass as MFA sign-in method with Microsoft work-accounts
Microsoft work-accounts / Azure AD easily integrate with Microsoft Authenticator for Multi-Factor Authentication. However, it is also possible to setup a third-party authenticator application for MFA. It just needs to implement the TOTP protocol.
KeePass, the well-known password manager, ships with a built-in support for TOTP protocol, making it good candidate for using in the MFA process. More, availability of keepass-third-party plugins help the embarking but even the “raw” KeePass, starting from the last version (2.51), can be easily used. Below the required steps.
The following step-by-step guide shows how to add KeePass as an authenticator-app. Existing methods will be not affected.
With a Microsoft work-account, login to https://myaccount.microsoft.com/ and select “Security Info”:
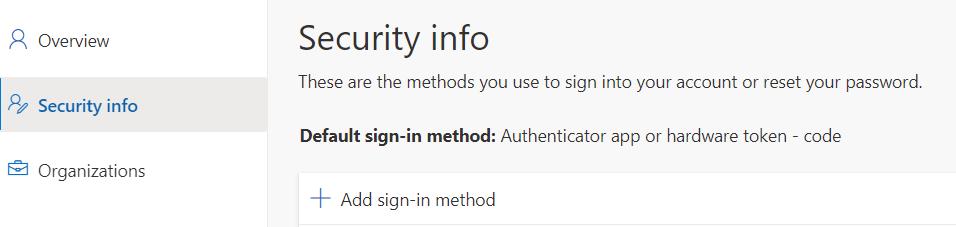
Select “Add sign-in method”:
Select “Authenticator app”:
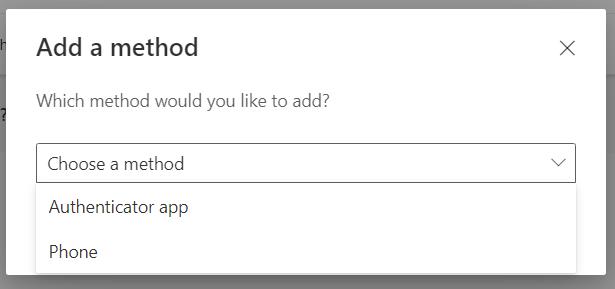
The wizard suggests using Microsoft Authenticator. Select “different authenticator app”:
Press Next.
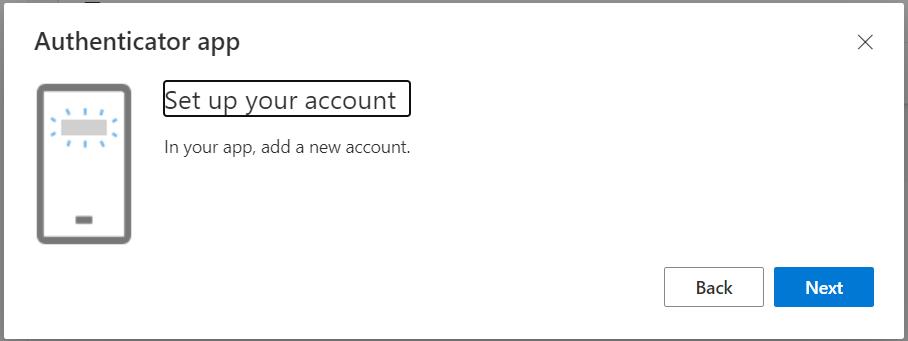
Normally, at this step, you should scan the QR code with your mobile phone app. But KeePass runs on a computer, and it is not able to scan it. Select “Can’t scan image?”.
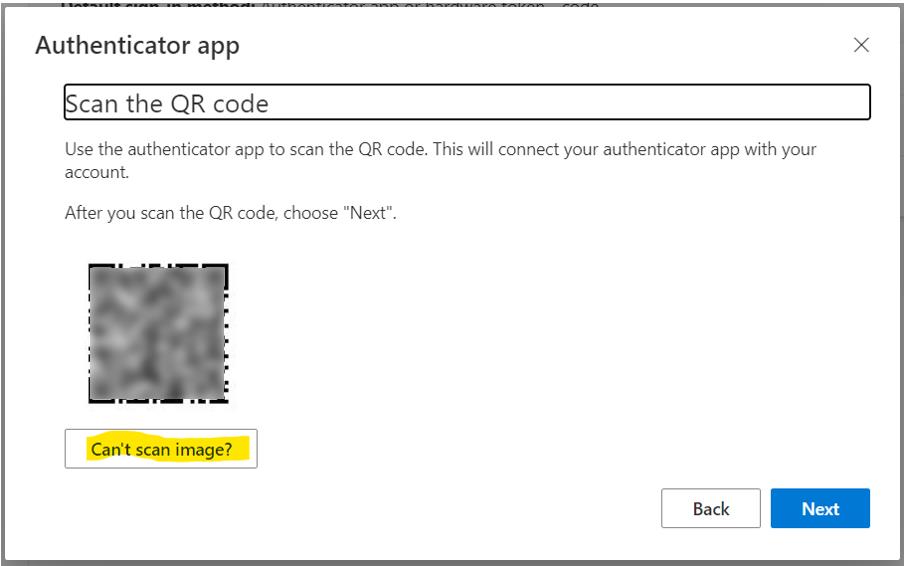
Now the website shows the very key-information we need to setup into the multi-factor-authentication application: the Secret Key. This is the information needed by TOTP protocol to work. Copy it, pressing the small icon on the right.
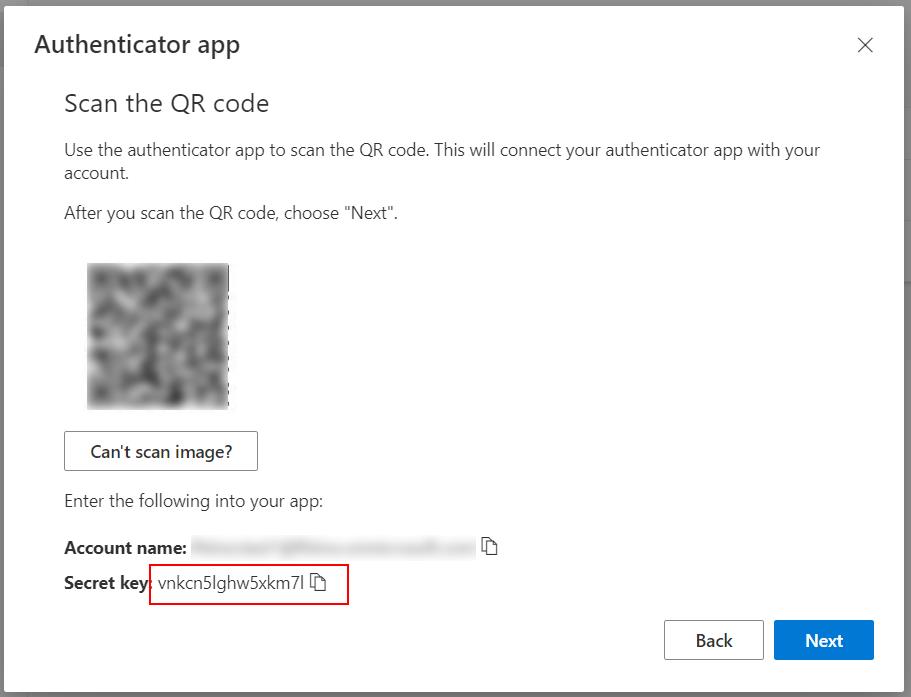
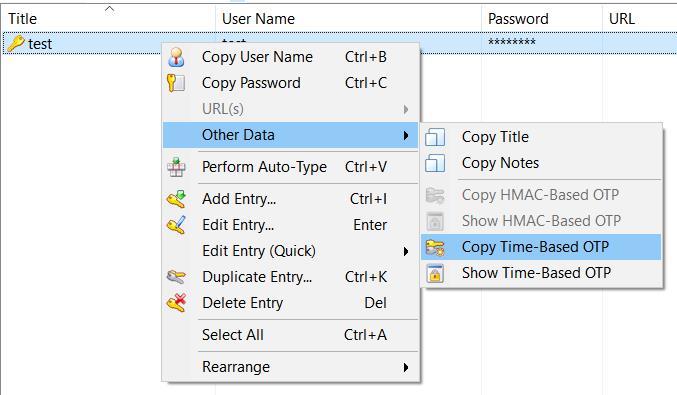
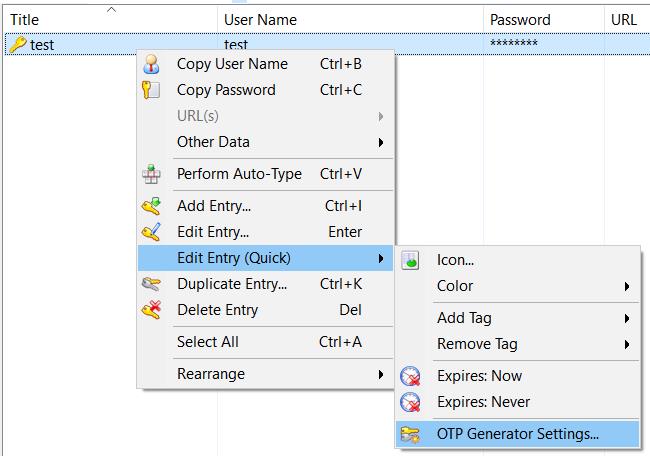
In KeepPass, right click on the entry where you want to store the code, select “Edit entry (quick)” –> OTP Generator Setting…
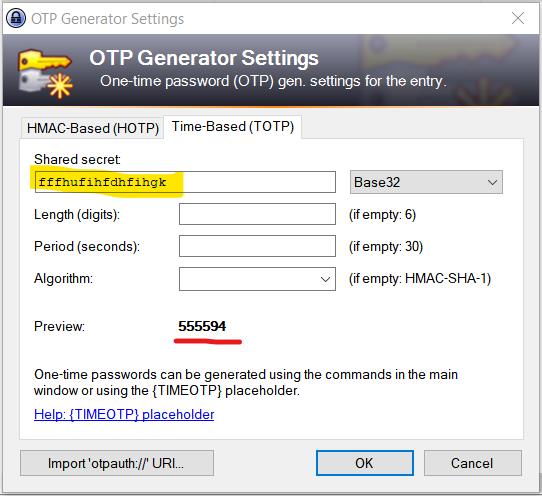
Copy the value into the field “Shared secret”. Do not modify the other options. KeePass immediately starts generating OTP values. They continue to change every 30 seconds.
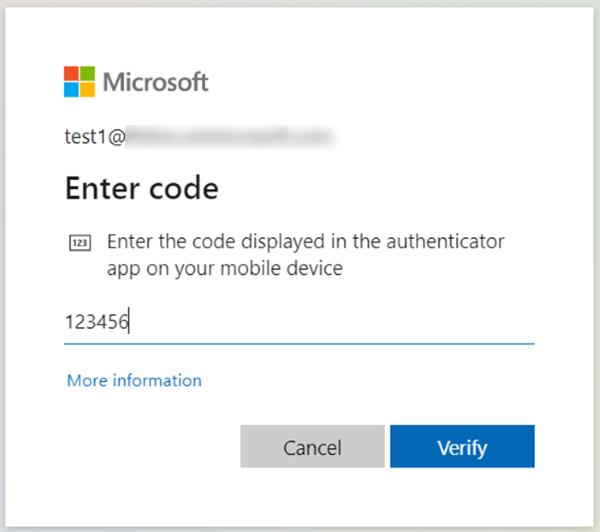
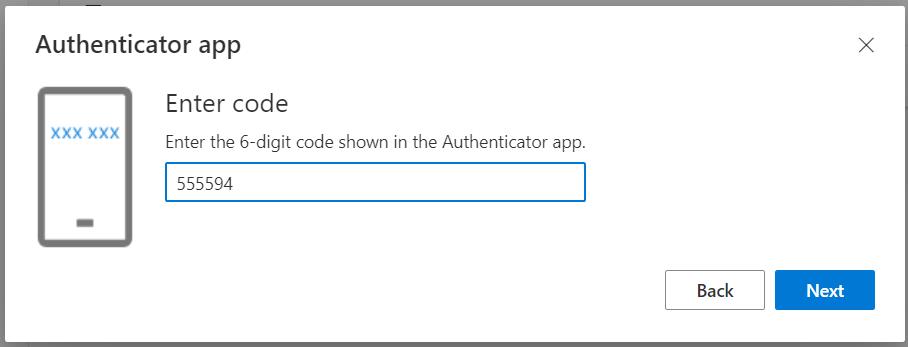
Go back to Microsoft account setup and press Next. You will be asked to enter the code. Copy the code generated by KeePass. Consider it changes every 30 seconds. Then press next.
If the code is recognized, a new “Authenticator app” row will appear among the other sign-in methods. Remember to press OK for confirming the entry in KeePass and save the updated KeePass database file.
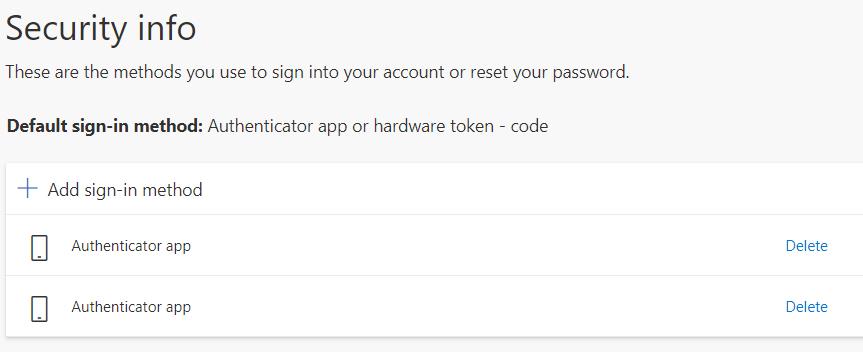
Note: the above user-interface is not very well designed. Currently it is missing the possibility of editing the name “Authenticator app” or adding a note in the central column (I assure, there is a “description” column!). Hope Microsoft will fix it in the next months. So, if you have more than one third-party authenticator, currently it is impossible to understand which row points to whom.
The setup process is completed. Using the KeePass during login is very easy. When asked for entering the code, right click on the KeePass entry –> “Other Data” –> “Copy Time-Base OTP”. This will generate the 6-digit code and copy it to clipboard. Paste it on the online form and press Verify.